
The science that aims to provide an evaluation of a specific digital asset and to extract information that might be helpful to address and assist an investigation related to the scenario depicted in that particular digital document is known as multimedia forensic. The ease, with which multimedia information may now be altered, including the emergence of deep fakes and other complex modifications, makes the field crucial. Thus, we have a comprehensive guidance on "why study multimedia forensics: the growing threat of digital crime."
Understanding Multimedia Forensics
As multimedia comprised with content combining graphics, text, video, and audio, digital forensics started encountering difficulties when applied to this subject. Due to the widespread usage of mobile devices, lower storage costs, and more bandwidth, internet users are producing enormous amounts of data. Digital multimedia has gained prominence as a result of this expansion. The volume of data is so enormous that it exceeds the forensic specialists' capacity to handle and evaluate it efficiently. These days, multimedia forensics is a crucial component of cyber forensics. The collection of methods used to analyze multimedia signals, such as audio, video, and photographs, is known as multimedia forensics. It seeks to:
- Information retrieval from multimedia signals
- Revealing the history of digital material
- Identifying the collection device that generated the data and
- Verifying the contents' integrity
What are the approaches to Multimedia Authentication?
Since there are many various types of internet information and it is not only text, the forensic techniques used to examine it must likewise be diverse. Here, the objective is to create a piece of logical forensic evidence by analyzing text, audio, video, and photographs. The two primary methods used by multimedia forensics are active image authentication and passive image authentication. Let's use an illustration to better grasp this.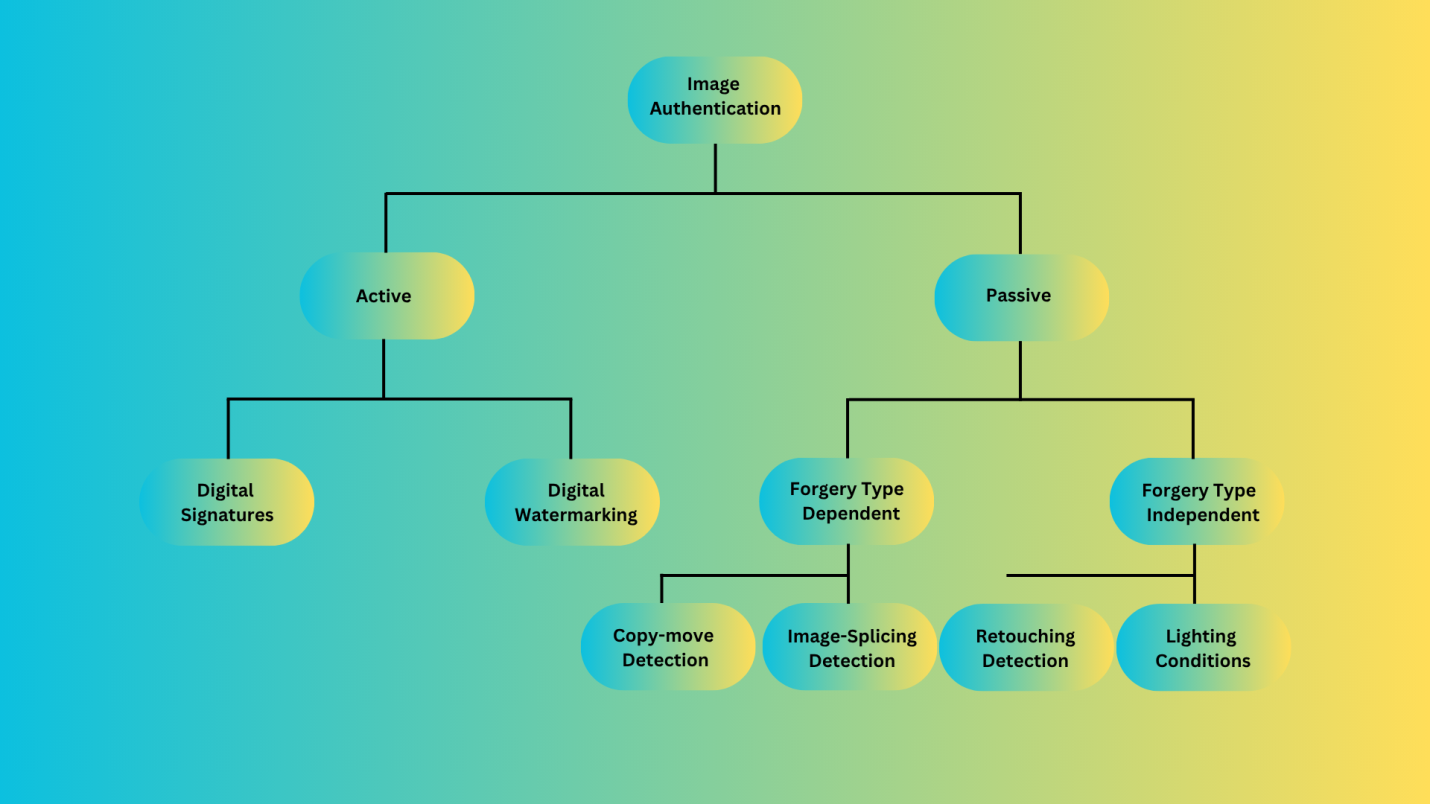
The graphic shows how Active and Passive image authentication are further separated into several types. Let's begin by going over each area in more depth.
Active Image Authentication:
In order to verify the integrity of the picture at the receiving end, a known authentication code is either supplied with the image or embedded in it during image production. By confirming this code, the image's uniqueness is confirmed. Digital watermarking and digital signatures are the two other categories under which active authentication falls. Active image authentication's disadvantages include:
- Prior knowledge of the image becomes essential as the authentication code must be placed in the image while recording using specialized equipment.
- This method's compatibility with specialized digital equipment is limited since it necessitates the creation of a digital watermark or digital signature at the same moment the image is captured.
- Since most photos on the Internet nowadays lack a digital signature or watermark, this image authentication approach has been compelled to take into account other methods. - Watermarking digitally: During picture acquisition or processing, a digital watermark is incorporated into the image using this approach. Digital Signatures: At the acquisition end, digital signatures incorporate some secondary information into the picture that is often derived from the image.
Passive Image Authentication:
picture forensics, another name for passive authentication, employs the one picture that has no previous information to determine the image's integrity. The premise behind passive authentication is that, even while altering the image would not leave any visible evidence, it is likely to change the underlying statistics. This implies that even when no tangible evidence has been left behind, digital forgeries have the potential to alter the image's fundamental qualities.
The Growing Threat of Digital Crime
One significant and growing concern is cybercrime. The more personal and corporate information we disclose online, the more opportunities there are for criminals to take it and exploit it for illicit activities and financial gain.
Understanding how cybercrime has grown to be such a significant issue, why we are all so susceptible to it and what we can do to protect ourselves are crucial as this danger continues to increase in our everyday lives.
Criminal action using computers, networks, and digital devices is referred to as cybercrime. It may endanger and damage people, companies, and national security. Particularly, a lot of individuals become victims of financial cybercrimes; this is a widespread issue that has affected a great number of lives. Additionally, we are becoming more and more susceptible to cybercrime risks as a result of our dependence on the internet and the World Wide Web.
You might not be aware that the internet and the World Wide Web are two distinct concepts if you're not a tech geek. An international network of linked computers is known as the Internet. The World Wide Web is a network of connected hypertext materials that we may access online. In any case, the two phrases are now almost synonymous.
The Internet and World Wide Web have brought a massive amount of information to thousand of millions of people all over the world. Due to the widespread popularity of the internet, more Americans claim that they would find it more difficult to give it up than to give up television.
Online communications have undoubtedly transformed the world. Positively, individuals can accomplish much more thanks to the internet, including gathering and sharing knowledge, promoting and selling items, and communicating in real time across long distances.
However, there are drawbacks to the Internet, such as the possibility of privacy invasions, bullying, and stalking. Furthermore, a growing wave of cybercrime was brought on by the storage and movement of electronic data, including personal information, credit card numbers, and other data.
Career Opportunities in Multimedia Forensics
We are surrounded by digital data, which is regularly gathered for most investigations. It's conceivable that someone who was involved in a crime utilized a computer, a cell phone, or the internet. Digital audio, photographic, and video recording equipment are also widely available; security cameras and gadgets are found in most enterprises and in many local and state governments, and they may produce a surprisingly large number of images and videos. Digital & Multimedia Sciences offers a number of specializations to satisfy this expanding need. In addition to performing and conducting digital forensic exams, specialists in the fields of digital and multimedia sciences also assist in the development of the scientific underpinnings for the practice of digital forensics, including research and publishing, and they may oversee digital forensic labs.
Scope of Work
In order to identify the many kinds of digital evidence, digital evidence exams need highly specialized apparatus and software. Depending on their areas of expertise, examiners may find evidence and testify about network analysis, digital device examinations, and the comparison and analysis of digital images, numbers, audio, and video (including photogrammetry, authenticity, and enhancement).
In the past, computer forensics only involved examining specific machines that could be connected to illegal behavior. To adequately examine and ascertain what transpired, network forensics is now necessary, even for mobile devices that offer fully networked computing capability in the palm of your hand. The methods and processes needed for audio recording analysis are still developing fields of study. Documenting crime scenes and injuries may be made easier with the introduction of digital photography.
Career Opportunities
Both the private as well as governmental sectors make effective use of digital forensic experts. Most large cities have private practice consultants. Digital forensic experts are generally engaged by the majority of police organizations as well as state and federal law enforcement agencies. Digital and multimedia scientists are employed or practicing as speech scientists, image analysts/examiners, facial recognition/biometrics, computer experts, video analysts/examiners, audio analysts/examiners, and computer-related criminal investigators.
Challenges and Future of Multimedia Forensics
Dealing with large and varied data sets, the growing complexity of anti-forensic methods, and the requirement for specialized knowledge are some of the difficulties multimedia forensics faces. According to several research studies, the future of multimedia forensics entails resolving privacy-related ethical concerns, creating standardized tools and procedures, and utilizing AI and machine learning for automated analysis.
Challenges in Multimedia Forensics:
Data Volume and Complexity: Forensic investigators must be able to effectively search and evaluate enormous volumes of digital data, which is always growing and can take many different forms (pictures, videos, audio, etc.).
Anti-Forensic Techniques: To evade detection and complicate investigations, criminals employ anti-forensic techniques such as data encryption, data wiping, and digital evidence manipulation.
Data Diversity and Storage: Because digital evidence may be found on a variety of devices and storage sites, investigators must modify their methods.
Ethical Issues: Three ethical issues that require attention include potential biases in the interpretation of forensic results, the abuse of evidence, and privacy problems.
Lack of Standardization: According to several research articles, the inability to compare and evaluate forensic results due to a lack of standardized equipment and procedures affects the admissibility of evidence in court.
Future of Multimedia Forensics:
AI and Machine Learning: Automation of data analysis, anomaly detection, and pattern recognition in digital evidence are all possible with AI and machine learning.
Cloud Forensics: It will be essential in the investigation of cybercrimes and the collection of evidence from cloud settings as cloud computing grows in popularity.
Quantum Computing: By expediting data processing and resolving intricate cryptographic issues, quantum computing has the potential to completely transform digital forensics.
Standardization and Cooperation: The effectiveness and dependability of digital investigations may be increased by creating standardized instruments and procedures and encouraging cooperation between law enforcement and forensic experts.
Ethical Training: It is crucial to give forensic specialists ethical training in order to handle privacy issues and guarantee appropriate data management.
Conclusion
Multimedia forensics has become an essential tool for locating, examining, and validating digital evidence in a world where digital interactions are taking over more and more of the conversation. It is impossible to overestimate the significance of this topic given the rise in cybercrimes, which include identity theft, deep fakes, data breaches, and disinformation. Traditional forensic methods by themselves are no longer enough because to the ongoing growth in the amount, complexity, and variety of digital material. A strong foundation for identifying tampering, authenticating digital information and providing reliable evidence to support legal investigations is provided by multimedia forensics.
This field is at the forefront of digital forensics, including everything from sophisticated analysis of audio, video, and photographic evidence to active and passive image authentication. By guaranteeing the validity and integrity of digital data, it not only plays a crucial part in crime investigation but also supports the rule of law.
Multimedia forensics offers a bright career path with plenty of prospects in law enforcement, government organizations, and the commercial sector for professionals and students wishing to pursue a career in cyber security or forensic science. The need for qualified professionals will only increase as the area develops with new technologies like artificial intelligence (AI), machine learning, cloud computing, and quantum systems.
By pursuing a degree in multimedia forensics, you're not only entering a technical sector but also strengthening the defenses against online fraud and creating a more secure and reliable digital environment.